This paper was presented at the Global Animals in Disaster Management Conference in July 2023.
Major disaster events such as hurricanes, floods, fires, earthquakes and tornadoes pose significant challenges to agricultural production every year. Commercial livestock and poultry operations are highly dependent on favourable environment, weather conditions and infrastructure to thrive. Adverse conditions during extreme weather events and other emergencies can result in significant loss of animals and commodities due to disruptions in utilities and critical services, facility damage, contamination of feed and water supplies, environmental extremes and biosecurity lapses. The effects on production can be long lasting and cumulative. Being able to identify, assess and mitigate potential vulnerabilities that lower risk helps organisations to prepare for and recover from these events. This paper provides an overview of the vulnerability assessment process in the United States that focuses on general and better practices that should be considered when applying these principles to commercial livestock and poultry operations. This approach has broad advantages for all countries where livestock and agriculture are exposed to these risks.
Introduction
‘Vulnerability’ is a term that generally means any part of an asset, system or organisation that is susceptible to damage, harm, disruption, or casualties when it is exposed to a hazard or threat (see OECD 1994). To understand this concept it is necessary to define some closely related terms that are frequently used to characterise or describe vulnerability. The Federal Emergency Management Agency (FEMA) (2004) determines ‘hazard’ as ‘a source of potential danger or adverse condition’. This differs from a threat, which FEMA defines as a ‘natural or man made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment, and/or property’ or a ‘natural or man-made source or cause of harm or difficulty’. The distinction is that a threat is directed at a specific target or asset, such as an operation or geographic area, whereas a hazard is less categorical or focused (United States Department of Homeland Security 2010). In either case, the resulting damage can be in the form of property loss, injuries, mortalities, business interruptions and added economic costs that are incurred during recovery efforts (Deyle and May 1998; ISO/IEC 2018).
Risk, on the other hand, represents the likelihood or measure of probability that damage or harm will occur and is an integral component of every vulnerability or security analysis. Formally defined by the United States Department of Homeland Security (2010), risk is the ‘potential for an adverse outcome assessed as a function of threats, vulnerabilities and consequences associated with an incident, event, or occurrence’. The level of risk can be influenced (and is often elevated) by vulnerabilities inherent to an organisation or system. Because of this relationship, completing a vulnerability assessment is a critical step in developing appropriate mitigations that minimise or eliminate risks due to different types of hazards.
In general, vulnerabilities can be categorised as physical or social factors. Physical factors are tangible, objective features that influence a specific organisation or system, while social factors tend to be subjective and conceptual. Examples of each are provided in Table 1. Some of these factors are difficult to control and cannot be effectively managed or changed to a degree that will significantly raise or lower vulnerability. As such, the primary emphasis of a vulnerability assessment should be directed at measures that successfully enhance an organisation’s resilience (e.g. ensuring the integrity of facilities and structures, maintaining stockpiles of essential supplies, developing options for emergency power and training and preparing staff).
Table 1: The physical and social factors that can categorise vulnerabilities.
| Physical factors | Social factors |
| Geographic location Topographical features Environmental factors (climate, wind patterns, etc.) Seasons and weather Vegetation and wildlife Facilities, structures and roadways Critical Infrastructure (utilities, resources, etc.) Enzootic pests and pathogens |
Population demographics Prior experience(s) (incidents, drills, near misses) Economic variables Business processes Legal frameworks Political factors Competition for resources High-risk behaviours and conditions Workforce and personnel |
A formal vulnerability assessment process entails characterising perceived weaknesses or deficiencies that are unique to a particular enterprise and then estimating their cumulative effects on risk (or the likelihood and effect of potential hazards). Assessments can be quantitative by assigning estimated or actual numerical values to potential hazards according to their likelihood and magnitude of damage. However, precise quantitative analysis may not always be possible and it may be necessary to categorise hazards qualitatively by assigning a descriptor or some other subjective measure to estimate their influence. Assessment results offer an organised comparison of how vulnerabilities affect risk and help to prioritise or rank response actions according to the anticipated level of harm (National Research Council 1983). By understanding and proactively assessing potential vulnerabilities, emergency managers and authorities can address apparent gaps that can be exploited to intensify the level of damage.
Agricultural animal production units are susceptible to a wide range of hazards, which include naturally occurring events like extreme weather, geological disturbances, pestilence and disease outbreaks. Hazards can also be associated with critical technology failures like hazardous materials spills, structural fires, utility disruptions, equipment breakdowns, security breaches and major infrastructure failures. The overall diversity of livestock and poultry operations, coupled with their vast size, scale, and complexity, introduces unique vulnerabilities that can drastically amplify the damage and destruction associated with these events and put agricultural businesses at disproportionately higher risks when disasters occur (Harper 2020).
Vulnerabilities can be assessed for an individual farm; group of farms; a discrete industry; a specific community; or at the state, national or international level. Within each sector, the level of vulnerability can vary between different work units, phases of the production cycle, animal populations and among various animals within a group. The integrity of the assessment process is highly dependent on accurately defining the critical processes needed to sustain a type of operation, commodity or population of interest. Increased vertical integration of some of these functions within agricultural sectors has intensified the vulnerabilities specific to these industries. The increasing rate of cross-dependence on common commodities and services (e.g. feed suppliers, transportation services, slaughter and processing facilities) creates bottlenecks within supply chains that can cause a relatively uncomplicated emergency to escalate into a major crisis. This was experienced during the COVID-19 pandemic when prolonged workforce disruptions in slaughter and processing plants in the USA triggered mass depopulations of swine and poultry (Hayes et al. 2021).
Vulnerability assessment process
The vulnerability assessment process begins by assigning a team of qualified individuals to conduct an in depth evaluation. The goal is to assemble a group of professionals from various backgrounds and disciplines who collectively represent the broad spectrum of skills and expertise needed to accurately analyse the condition and performance of the organisation. Examples include farmers and producers, veterinarians, university faculty representatives, agricultural extension staff, safety practitioners, information technology experts, security experts, animal transportation service providers, feed mill operators and processing plant managers. Local and regional law enforcement agencies, fire departments and emergency management officials should also be included to ensure they understand each animal program’s needs and capabilities and any limitations of local emergency response service providers to meet these expectations.
Emergency and disaster planning is a critical mission element of several USA government agencies (e.g. Department of Homeland Security, Federal Emergency Management Agency; Department of Agriculture, Animal and Plant Inspection Service; Department of Health and Human Services, Centers for Disease Control and Prevention and the Administration for Strategic Preparedness and Response; and Department of Commerce, National Oceanic and Atmospheric Administration). These agencies, in partnership with local, regional and tribal governments; professional societies (e.g. American Veterinary Medical Association, state veterinary medical associations); industry stakeholders and producer groups (e.g. American Dairy Association, American Egg Board, National Pork Producers Council, National Cattlemen’s Beef Association, American Poultry Association); humanitarian organisations (e.g. American Red Cross, animal shelters, animal rescue groups) and academia (e.g. land-grant universities, Agricultural Extension Service) have developed tools and resources to assist farmers and producers who are preparing for different types of emergency situations. Those participating in the vulnerability assessment often use these resources to develop customised templates or checklists that can be used during evaluations of properties, facilities, equipment, work practices and personnel.
Assessments should be repeated regularly at defined intervals and after every incident or ‘near miss’ experience to determine potential vulnerabilities associated with that event. Specific attention should be given to:
- the construction and integrity of physical structures (barns, fence lines, storage systems)
- the location and condition of vegetation and landscaping features (trees, brush, organic debris)
- potable water sources (rivers, ponds, streams, storage tanks, water treatment systems)
- the access to transportation routes (highways, railroads, waterways, unpaved roads, etc.)
- the status of critical equipment (vehicles, ventilation systems, generators, pumps)
- essential utilities and services (electrical power, communication systems, internet services)
- standard operating procedures (feeding schedules, daily animal observations, veterinary care)
- staffing logistics (personnel training, scheduling and availability).
The condition of all critical facility infrastructure systems (water, power, communications networks), including primary units and availability of ancillary backup systems, should be noted as part of the inventory.
Inevitably, new and previously unidentified vulnerabilities often surface as the result of external or internal influences over time.
Therefore, it is essential that emergency response plans are exercised and updated regularly, given that new vulnerabilities can emerge each time a plan is activated, new vulnerabilities can emerge. It is preferable that this occurs during an exercise phase rather than during an actual event to maintain operations integrity. In addition to large-scale emergency response exercises, table-top exercises and drills used as practice sessions to train staff and test the effectiveness of plans can also serve to highlight vulnerabilities. Independent third-party observers should be assigned to watch and critique staff as they implement delegated response actions. The feedback they provide can be used to update plans and reinforce training efforts. Uniformly, a debriefing should be conducted every time the plan is deployed to explore all factors that contributed to the outcome and to identify any actions that need to be taken to lower future risk.
Data analysis
After completing a comprehensive inventory of potential vulnerabilities, the organisation under evaluation needs to analyse the individual and collective effect of each on essential business functions. A quantitative approach can be used, by creating a vulnerability assessment checklist that lists an organisation’s assets (e.g. buildings, site, systems, functions) and then estimates the potential loss or damage that each could incur during a hazard or threat event. The vulnerabilities for each asset can be ranked on a low-to-high scale, based on the degree of susceptibility or weakness assigned to that asset under various conditions (FEMA n.d.1). Such an analysis helps to stratify vulnerabilities and enables down selection to focus mitigation efforts on a subset of higher-consequence vulnerabilities that warrant further consideration. The analysis can be expanded to inform all aspects of an organisation’s emergency preparations. For example, risk may be assessed and quantitatively compared as it relates to asset value, threat rating and/or vulnerability rating (FEMA n.d.2). A risk matrix (see Figure 1) is useful to prioritise mitigation activities. The matrix depicts the likelihood of a vulnerability being exploited against the outcome of exploiting the vulnerability (Federal Aviation Administration 2018). The results are shown using a visual (e.g. colour) scale that qualitatively demonstrates the various outcomes.
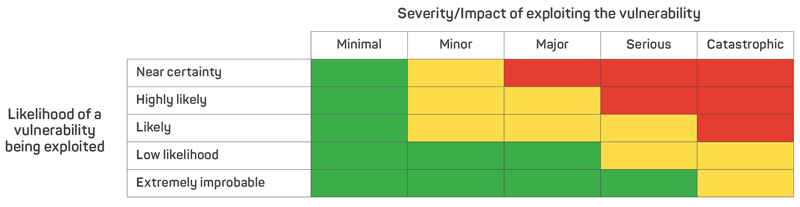
Figure 1. Example risk matrix showing high-, medium- and low-level risks depicted as red, yellow and green, respectively.
Source: Adapted from Federal Aviation Administration (2018)
Effects should be assessed under a variety of conditions, ranging from minimal damage to 'worst case’ scenario. Results should be used to develop and prioritise tactical control measures that can be implemented to reduce or manage vulnerability. Precedence should be given to efforts that maintain critical infrastructure and services necessary to continue fundamental operations and core business functions. Ideally, plans should be scalable, flexible and adaptable to respond appropriately to a full spectrum of hazards (or combination of hazards) ranging from minor, isolated incidents to major, comprehensive disasters.
Elimination of hazards whenever possible is always the preferred option. Examples include locating buildings and storage tanks away from flood or seismically active zones, removing dried brush and excessive vegetation that obstructs visibility or increases fire hazards around property perimeters and buildings and securing structural elements (e.g. shingles, fence panels, hinged gates) and other loose debris (e.g. tree limbs, building materials, feed troughs) that can become airborne during high winds. However, elimination may not always be an option for some hazards that are outside the organisation’s sphere of influence. In these cases, plans should include opportunities to minimise the likelihood and/or effect of hazards through mitigation procedures. Vulnerability can be significantly reduced through simple measures such as maintaining property fence lines; installing lightning suppression systems on buildings and tall metal structures and making sure buildings, barns and vehicles have a working fire extinguisher or fire suppression system.
Analysis should consider mitigation activities that might fail by adding redundancy and alternate control measures that can be substituted during extreme circumstances. Extended loss of some critical systems can amplify damage and loss over time, so installing early warning systems and alarms that give advance notice that a system may be compromised is critical to provide a timely response. Having access to fuel-powered generators during extended utility or service disruptions can provide power to life support systems for animals raised in confinement (e.g. ventilation systems, pumps, feed conveyors). Vehicles and trailers needed to transport animals, supplies and personnel should be accessible and maintained in good working condition with adequate fuel supplies available for extended operation. Secondary containment systems (e.g. earth dikes, sumps, berms, retaining walls, drip trays) should be installed around systems used to store hazardous materials to minimise the effects of leaks or spills. In addition, communication systems (e.g. line-based systems, mobile phones, mass media, email) may not function because of network failures due to peak use or damage. Multiple alternative communications (e.g. short-wave radio, two-way radio, internet-based communication, sirens) should be available and the line of decision-making authority should be clearly defined to provide timely and continuous exchange of information.
The size, unpredictable temperament and relatively large group sizes of agricultural animals maintained in a production unit represent major vulnerabilities that significantly limit emergency response options. Some livestock may be raised in free-ranging herds or flocks on open fields that impede efforts to secure these animals in a timely and efficient manner. Attempts to physically move animals to another location are often not successful because of the demands on skilled workers, vehicles, trailers and other equipment, combined with challenges identifying an adequately equipped relocation site capable of receiving and caring for transported animals. Consequently, sheltering-in-place until the emergency subsides may be the only practical option available to many establishments.
Maintaining biosecurity is another challenge due to the increased and unplanned movement of animals, people and equipment during emergency conditions. Significant environmental and public health concerns can ensue due to indiscriminate pathogen release, carcass disposal, nutrient runoff and groundwater contamination, often progressing into secondary emergencies that complicate response efforts. Vulnerable resources (e.g. drinking water, feed components, pastures for grazing) should be managed in a way that prevents spoilage and inadvertent contamination by pathogens, chemicals or other foreign materials. Developing plans to manage animal carcasses that accumulate during periods of increased mortality should include options for safely burying, composting or incinerating them onsite until conditions return to normal.
Applying results
Agricultural animal producers should establish ‘good faith’ agreements with local authorities and response agencies in the understanding that these organisations can become overwhelmed by humanitarian concerns that may exhaust available resources during large-scale disasters. Circumstances may quickly deteriorate, leaving agricultural-based businesses to manage response efforts autonomously. Workload and essential skill requirements should be assessed to determine minimum staffing levels required to maintain basic operations, immediately and over an extended timeframe. Some workers may have competing concerns (e.g. pre-existing health conditions, family care responsibilities, financial obligations) or logistics challenges (e.g. limited transportation options, scheduling constraints, language barriers) that interfere with their ability to contribute to the response effort. Remaining personnel may be required to cover for those who are absent and are likely to become physically and mentally fatigued during prolonged emergency operations. This emphasises the importance of managing work assignments that also considers the vulnerability of individual workers.
After plans are implemented, regular review sessions should be convened to evaluate the effectiveness of local policies and procedures. All written standard operating procedures, checklists, and inventory records (e.g. animals, supplies, equipment, personnel, supplies) will inform the review process. The results of inspections (e.g. premises, facilities, equipment, storage areas), training exercises, incident reports and near misses should be compared to the content of plans to identify new or previously unidentified hazards and vulnerabilities that affect location preparation or the competency of personnel. All practices should be aligned with relevant regulations and policies related to emergency response.
An effective response effort reflects the collective skills and abilities of individual team members whose actions can have profound consequences on the outcome. Providing training to individuals assigned to be part of the response effort helps to minimise vulnerabilities due to staff error and inexperience. The process should be part of the introduction program for new personnel and repeated at regular intervals as refresher training for veteran staff. A variety of training methods that appeal to the different strengths, styles and learning preferences of students should be used. Options include self directed (or self-paced) online modules, live lectures, videos, webinars, podcasts and hands on training for individuals or groups. Table-top exercises and simulated drills are an excellent way to review plans and evaluate the team’s ability to take action and make decisions under pressure. FEMA developed a Homeland Security Exercise and Evaluation Program that ‘provides a set of guiding principles for exercise and evaluation programs as well as a common approach for exercise program management, design and development, conduct, evaluation, and improvement planning’ (FEMA 2020).
Near misses or actual events that require a response plan to be activated provide opportunities to learn about vulnerabilities relative to design or implementation. An informal ‘hotwash’ should be performed immediately after planned or unplanned incidents to capture the feedback of every person involved. The session should be brief and focus on immediate concerns such as the health and safety of participants, conditions of animals and other assets and safety or security concerns. Later, this should be followed by an in-depth analysis organised as a structured debriefing or after action review to compare participants’ experiences during the incident and what happened. The process should involve a neutral facilitator who maintains a non-threatening environment. This is appropriate for personal self-reflection and constructive dialogue that will enhance team performance.
Lessons learnt through formal and informal self-assessments should be used to guide the revision of plans and to address perceived vulnerabilities. Continuous evaluation that is informed by training exercises, drills, near misses and actual incident reviews provide avenues to expose deficiencies that might go undetected. Comparing plans across organisations that face similar vulnerabilities promotes timely adoption of practices and technologies that can enhance the effectiveness of response plans and activities.
Conclusion
Vulnerability describes the intrinsic flaws or weaknesses in an organisation or system that make it susceptible to harm or damage when challenged. Identifying vulnerabilities and estimating their effect helps to guide actions that can be taken to minimise or negate the potential hazards on farms, in communities or at the national level. Many vulnerabilities that apply to farms and agriculture are difficult to control. The most common management options include maintaining disaster-ready facilities and structures, developing alternatives for critical services, implementing lessons though experience and continuously assessing worker performance and behaviours. A multi disciplinary vulnerability assessment team serves as a constructive feedback mechanism to inform these processes and should be employed to analyse the susceptibility of an organisation or system to various hazards and threats.


